 W
WAuthentication is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product or document is not counterfeit.
 W
WA cryptocurrency, crypto-currency, or crypto is a binary data designed to work as a medium of exchange wherein individual coin ownership records are stored in a ledger existing in a form of a computerized database using strong cryptography to secure transaction records, to control the creation of additional coins, and to verify the transfer of coin ownership. Some crypto schemes use validators to maintain the cryptocurrency. In a proof-of-stake model, owners put up their tokens as collateral. In return, they get authority over the token in proportion to the amount they stake. Generally, these token stakers get additional ownership in the token over time via network fees, newly minted tokens or other such reward mechanisms. Cryptocurrency does not exist in physical form and is typically not issued by a central authority. Cryptocurrencies typically use decentralized control as opposed to a central bank digital currency (CBDC). When a cryptocurrency is minted or created prior to issuance or issued by a single issuer, it is generally considered centralized. When implemented with decentralized control, each cryptocurrency works through distributed ledger technology, typically a blockchain, that serves as a public financial transaction database.
 W
WA digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. A valid digital signature, where the prerequisites are satisfied, gives a recipient very strong reason to believe that the message was created by a known sender (authentication), and that the message was not altered in transit (integrity).
 W
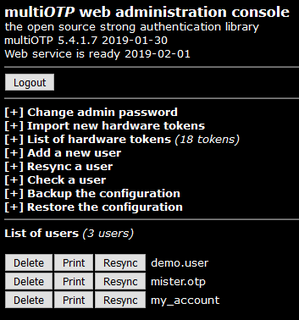
WmultiOTP is an open source PHP class, a command line tool and a web interface that can be used to provide an operating system independent strong authentication system. multiOTP is OATH certified since version 4.1.0 and is developed under the LGPL license. Starting with version 4.3.2.5, multiOTP open source is also available as a virtual appliance - as a standard OVA file, a customized OVA file with open-vm-tools, and also as an Hyper-V downloadable file.
 W
WOpenPuff Steganography and Watermarking, sometimes abbreviated OpenPuff or Puff, is a free steganography tool for Microsoft Windows created by Cosimo Oliboni and still maintained as independent software. The program is notable for being the first steganography tool that:lets users hide data in more than a single carrier file. When hidden data are split among a set of carrier files you get a carrier chain, with no enforced hidden data theoretical size limit implements 3 layers of hidden data obfuscation extends deniable cryptography into deniable steganography
 W
WSignals intelligence operational platforms are employed by nations to collect signals intelligence, which is intelligence-gathering by interception of signals, whether between people or between machines, or mixtures of the two. As sensitive information is often encrypted, signals intelligence often involves the use of cryptanalysis. However, traffic analysis—the study of who is signalling whom and in what quantity—can often produce valuable information, even when the messages themselves cannot be decrypted.
 W
WA steganography software tool allows a user to embed hidden data inside a carrier file, such as an image or video, and later extract that data.
 W
WTruth & Transparency Foundation is a whistleblowing organization inspired by WikiLeaks, which focuses on exposing documents from the leadership of The Church of Jesus Christ of Latter-day Saints. It began in October 2016 as a leaked series of videos on the YouTube channel Mormon Leaks. In total, 15 videos were initially leaked via the Mormon Leaks channel from meetings of high-ranking LDS leaders including the Quorum of the Twelve. They discussed topics including the "homosexual agenda", the subprime mortgage crisis, and a debate over the sexual orientation of Chelsea Manning. Politicians featured in the videos included former Utah governor Mike Leavitt and former U.S. Senator from Oregon Gordon H. Smith.
 W
WWikiLeaks is an international non-profit organisation that publishes news leaks and classified media provided by anonymous sources. Its website, initiated in 2006 in Iceland by the organisation Sunshine Press, stated in 2015 that it had released online 10 million documents in its first 10 years. Julian Assange, an Australian Internet activist, is generally described as its founder and director. Since September 2018, Kristinn Hrafnsson has served as its editor-in-chief.
 W
WITU-T Recommendation X.1035 specifies a password-authenticated key agreement protocol that ensures mutual authentication of two parties by using a Diffie–Hellman key exchange to establish a symmetric cryptographic key. The use of Diffie-Hellman exchange ensures perfect forward secrecy—a property of a key establishment protocol that guarantees that compromise of a session key or long-term private key after a given session does not cause the compromise of any earlier session.
 W
W