 W
WThe ANOM sting operation is a collaboration by law enforcement agencies from several countries, running between 2018 and 2021, that intercepted millions of messages sent through the supposedly secure smartphone-based messaging app ANOM. The ANOM service was widely used by criminals, but instead of providing secure communication, it was actually a trojan horse covertly distributed by the United States Federal Bureau of Investigation (FBI) and the Australian Federal Police (AFP), enabling them to monitor all communications. Through collaboration with other law enforcement agencies worldwide, the operation resulted in the arrest of over 800 suspects allegedly involved in criminal activity, in 16 countries. Among the arrested people were alleged members of Australian-based Italian mafia, Albanian organised crime, outlaw motorcycle clubs, drug syndicates and other organised crime groups.
 W
WThe Automatic Certificate Management Environment (ACME) protocol is a communications protocol for automating interactions between certificate authorities and their users' web servers, allowing the automated deployment of public key infrastructure at very low cost. It was designed by the Internet Security Research Group (ISRG) for their Let's Encrypt service.
 W
WConfide is an encrypted instant messaging application for most major operating systems. It was first released in 2013 on iOS, and is known for its self-destructing messaging system that deletes messages immediately after reading. The platform offers both free and paid features for individuals and businesses.
 W
WCSipSimple is a Voice over Internet Protocol (VoIP) application for Google Android operating system using the Session Initiation Protocol (SIP). It is open source and free software released under the GNU General Public License.
 W
WThe Defense Red Switch Network (DRSN) is a dedicated telephone network which provides global secure communication services for the command and control structure of the United States Armed Forces. The network is maintained by the Defense Information Systems Agency (DISA) and is secured for communications up to the level of Top Secret SCI.
 W
WDomain fronting is a technique for Internet censorship circumvention that uses different domain names in different communication layers of an HTTPS connection to discreetly connect to a different target domain than is discernable to third parties monitoring the requests and connections.
 W
WGuardian Project is a global collective of software developers, designers, advocates, activists and trainers who develop open-source mobile security software and operating system enhancements. They also create customized mobile devices to help individuals communicate more freely and protect themselves from intrusion and monitoring. The effort specifically focuses on users who live or work in high-risk situations and who often face constant surveillance and intrusion attempts into their mobile devices and communication streams.
 W
WiGap is a free Iranian instant messaging application for smart phones and personal computers. iGap allows users to interact with each other and exchange information through text, image, video, audio and other types of messages. iGap also supports P2P-based voice calls over the internet.
 W
WThe Librem 5 is a smartphone manufactured by Purism that is part of their Librem line of products. The phone is designed with the goal of using free software whenever possible, includes PureOS, a Linux operating system by default, and as of 2021 is the only smartphone recommended by the Free Software Foundation. Like other Librem products, the Librem 5 focuses on privacy and freedom, and includes features like hardware kill switches, and easily-replaceable components. Its name, with a numerical "5", refers to its screen size, and not a release version. After an announcement on August 24, 2017, the distribution of developer kits and limited pre-release models occurred throughout 2019 and most of 2020. The first mass-production version of the Librem 5 was shipped on November 18, 2020.
 W
WLinoma Software was a developer of managed file transfer and encryption solutions. The company was acquired by HelpSystems in June 2016. Mid-sized companies, large enterprises and government entities use Linoma's solutions to protect sensitive data and comply with data security regulations such as PCI DSS, HIPAA/HITECH, SOX, GLBA and state privacy laws. Linoma's software runs on a variety of platforms including Windows, Linux, UNIX, IBM i, AIX, Solaris, HP-UX and Mac OS X.
 W
WMailfence is an encrypted email service that offers OpenPGP based end-to-end encryption and digital signatures. It was launched in November 2013 by ContactOffice Group, which has been operating an online collaboration suite for universities and other organizations since 1999.
 W
WMix networks are routing protocols that create hard-to-trace communications by using a chain of proxy servers known as mixes which take in messages from multiple senders, shuffle them, and send them back out in random order to the next destination. This breaks the link between the source of the request and the destination, making it harder for eavesdroppers to trace end-to-end communications. Furthermore, mixes only know the node that it immediately received the message from, and the immediate destination to send the shuffled messages to, making the network resistant to malicious mix nodes.
 W
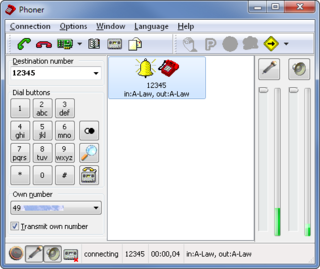
WPhoner and PhonerLite are softphone applications for Windows operating systems available as freeware. Phoner is a multiprotocol telephony application supporting telephony via CAPI, TAPI and VoIP, while PhonerLite provides a specialized and optimized user interface for VoIP only. Beside the different user interface focus both programs share the same code base.
 W
WPhoner and PhonerLite are softphone applications for Windows operating systems available as freeware. Phoner is a multiprotocol telephony application supporting telephony via CAPI, TAPI and VoIP, while PhonerLite provides a specialized and optimized user interface for VoIP only. Beside the different user interface focus both programs share the same code base.
 W
WProtonMail is an end-to-end encrypted email service founded in 2013 in Geneva, Switzerland by scientists who spent time at the CERN research facility. ProtonMail uses client-side encryption to protect email content and user data before they are sent to ProtonMail servers, unlike other common email providers such as Gmail and Outlook.com. The service can be accessed through a webmail client, the Tor network, or dedicated iOS and Android apps.
 W
WRetroshare is a free and open-source peer-to-peer communication and file sharing app based on a friend-to-friend network built on GNU Privacy Guard (GPG). Optionally, peers may communicate certificates and IP addresses to and from their friends.
 W
WSecure Terminal Equipment (STE) is the U.S. government's current, encrypted telephone communications system for wired or "landline" communications. STE is designed to use ISDN telephone lines which offer higher speeds of up to 128 kbit/s and are all digital. The greater bandwidth allows higher quality voice and can also be utilized for data and fax transmission through a built-in RS-232 port. STE is intended to replace the older STU-III office system and the KY-68 tactical system. STE sets are backwards compatible with STU-III phones, but not with KY-68 sets.
 W
WSecure voice is a term in cryptography for the encryption of voice communication over a range of communication types such as radio, telephone or IP.
 W
WSignal is a cross-platform centralized encrypted instant messaging service developed by the Signal Technology Foundation and Signal Messenger LLC. Users can send one-to-one and group messages, which can include files, voice notes, images and videos. It can also be used to make one-to-one and group voice and video calls, and the Android version can optionally function as an SMS app.
 W
WThe STU-I, like its successors sometimes known as a "stew phone", was a secure telephone developed by the U.S. National Security Agency for use by senior U.S. government officials in the 1970s.
 W
WThe STU-II is a secure telephone developed by the U.S. National Security Agency. It permitted up to six users to have secure communications, on a time-shared basis. It was made by ITT Defense Communications, Nutley, New Jersey. An OEM partner was Northern Telecom.
 W
WTor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than six thousand relays, for concealing a user's location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace the Internet activity to the user. Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities unmonitored.
 W
WTox is a peer-to-peer instant-messaging and video-calling protocol that offers end-to-end encryption. The stated goal of the project is to provide secure yet easily accessible communication for everyone. A reference implementation of the protocol is published as free and open-source software under the terms of the GNU GPL-3.0-or-later.
 W
WTutanota is an end-to-end encrypted email software and freemium hosted secure email service. Its motto is "einfach.sicher.mailen" in German, meaning "easy.secure.mailing".
 W
WTwinkle is a free and open-source app for voice communications over Voice over IP (VoIP) protocol. It is designed for Linux operating systems and uses the Qt toolkit for its graphical user interface. For call signaling it employs the Session Initiation Protocol (SIP). It also features direct IP-to-IP calls. Media streams are transmitted via the Real-time Transport Protocol (RTP) which may be encrypted with the Secure Real-time Transport Protocol (SRTP) and the ZRTP security protocols.
 W
WITU-T Recommendation X.1035 specifies a password-authenticated key agreement protocol that ensures mutual authentication of two parties by using a Diffie–Hellman key exchange to establish a symmetric cryptographic key. The use of Diffie-Hellman exchange ensures perfect forward secrecy—a property of a key establishment protocol that guarantees that compromise of a session key or long-term private key after a given session does not cause the compromise of any earlier session.
 W
WZooko's triangle is a trilemma of three properties that are generally considered desirable for names of participants in a network protocol:Human-meaningful: Meaningful and memorable (low-entropy) names are provided to the users. Secure: The amount of damage a malicious entity can inflict on the system should be as low as possible. Decentralized: Names correctly resolve to their respective entities without the use of a central authority or service.