 W
WAn advanced persistent threat (APT) is a stealthy threat actor, typically a nation state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period. In recent times, the term may also refer to non-state-sponsored groups conducting large-scale targeted intrusions for specific goals.
 W
WThe Anti Security Movement is a movement opposed to the computer security industry. Antisec is against full disclosure of information relating tosoftware vulnerabilities, exploits, exploitation techniques, hacking tools, attacking public outlets and distribution points of that information. The general thought behind this is that the computer security industry uses full disclosure to profit and develop scare-tactics to convince people into buying their firewalls, anti-virus software and auditing services.
 W
WAOHell was a Windows application that was used to simplify 'cracking' using AOL.
 W
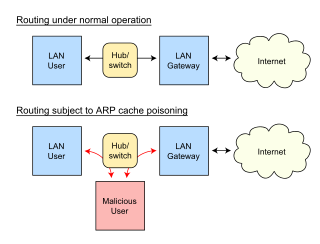
WIn computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.
 W
WMustafa Al-Bassam is a British computer security researcher and hacker. He co-founded the hacker group LulzSec in 2011, which was responsible for several high profile breaches. He later went on to co-found Chainspace, a company implementing a smart contract platform, which was acquired by Facebook in 2019. He is currently a PhD student in the Information Security Research Group at University College London working on peer-to-peer systems. Forbes listed Al-Bassam as one of the 30 Under 30 entrepreneurs in technology in 2016.
 W
WBBS: The Documentary is a 3-disc, 8-episode documentary about the subculture born from the creation of the bulletin board system (BBS) filmed by computer historian Jason Scott of textfiles.com.
 W
WMathew Bevan is a British hacker from Cardiff, Wales. In 1996 he was arrested for hacking into secure U.S. Government networks under the handle Kuji. At the age of 21, he hacked into the files of the Griffiss Air Force Base Research Laboratory in New York.
 W
WLoyd Blankenship, better known by his pseudonym The Mentor, is a well-known computer hacker and writer. He has been active since the 1970s, when he was a member of the hacker groups Extasyy Elite and Legion of Doom.
 W
WClickjacking is a malicious technique of tricking a user into clicking on something different from what the user perceives, thus potentially revealing confidential information or allowing others to take control of their computer while clicking on seemingly innocuous objects, including web pages.
 W
WClimatic Research Unit documents including thousands of e-mails and other computer files were stolen from a server at the Climatic Research Unit of the University of East Anglia in a hacking incident in November 2009. The documents were redistributed first through several blogs of global warming deniers, who alleged that the documents indicated misconduct by leading climate scientists. A series of investigations rejected these allegations, while concluding that CRU scientists should have been more open with distributing data and methods on request. Precisely six committees investigated the allegations and published reports, finding no evidence of fraud or scientific misconduct. The scientific consensus that global warming is occurring as a result of human activity remained unchanged by the end of the investigations.
 W
WConvicted computer criminals are people who are caught and convicted of computer crimes such as breaking into computers or computer networks. Computer crime can be broadly defined as criminal activity involving information technology infrastructure, including illegal access, illegal interception, data interference, systems interference, misuse of devices, forgery and electronic fraud.
 W
WThe Computer Misuse Act 1990 is an Act of the Parliament of the United Kingdom, introduced partly in response to the decision in R v Gold & Schifreen (1988) 1 AC 1063. Critics of the bill complained that it was introduced hastily and was poorly thought out. Intention, they said, was often difficult to prove, and that the bill inadequately differentiated "joyriding" hackers like Gold and Schifreen from serious computer criminals. The Act has nonetheless become a model from which several other countries, including Canada and the Republic of Ireland, have drawn inspiration when subsequently drafting their own information security laws, as it is seen "as a robust and flexible piece of legislation in terms of dealing with cybercrime”. Several amendments have been passed to keep the Act up to date.
 W
WCross-site scripting (XSS) is a type of security vulnerability that can be found in some web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec up until 2007. XSS effects vary in range from petty nuisance to significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner network.
 W
WThe Cuckoo's Egg: Tracking a Spy Through the Maze of Computer Espionage is a 1989 book written by Clifford Stoll. It is his first-person account of the hunt for a computer hacker who broke into a computer at the Lawrence Berkeley National Laboratory (LBNL).
 W
WCyber ShockWave, similar to the Cyber Storm Exercise, was a 4-hour wargame conducted in February 2010 by the Bipartisan Policy Center, an American think tank based in Washington, D.C. Former high-ranking Cabinet and National Security Officials role played a cabinet level response to a cyberwarfare scenario. Portions of the exercise were later broadcast on CNN.
 W
WCyberstrategy 3.0 is the United States information warfare strategy against cyberwarfare. This strategy uses deterrence based on making infrastructure robust and redundant enough to survive any Internet cyber attack. A good example of this concept can be seen in action in a cyber strategy game like CyberStratG.
 W
WCyberwarfare is the use of digital attacks to attack a nation, causing comparable harm to actual warfare and/or disrupting the vital computer systems. There is significant debate among experts regarding the definition of cyberwarfare, and even if such a thing exists. One view is that the term "cyberwarfare" is a misnomer, since no offensive cyber actions to date could be described as "war". An alternative view is that "cyberwarfare" is a suitable label for cyber attacks which cause physical damage to people and objects in the real world.
 W
WDecocidio #ϴ is an anonymous, autonomous collective of hacktivists which is part of Earth First!, a radical environmental protest organisation, and adheres to Climate Justice Action. In their hacks the group shows affiliation with the autonomous Hackbloc collective.
 W
WDaniel Domscheit-Berg, previously known under the pseudonym Daniel Schmitt, is a German technology activist. He is best known as the author of Inside WikiLeaks: My Time with Julian Assange at the World's Most Dangerous Website (2011).
 W
WAlbert Gonzalez is an American computer hacker and computer criminal who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATM numbers from 2005 to 2007: the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing attacks which allowed him to steal computer data from internal corporate networks. During his spree, he was said to have thrown himself a $75,000 birthday party and complained about having to count $340,000 by hand after his currency-counting machine broke. Gonzalez stayed at lavish hotels but his formal homes were modest.
 W
WHack Forums is an Internet forum dedicated to discussions related to hacker culture and computer security. The website ranks as the number one website in the "Hacking" category in terms of web-traffic by the analysis company Alexa Internet. The website has been widely reported as facilitating online criminal activity, such as the case of Zachary Shames, who was arrested for selling keylogging software on Hack Forums in 2013 which was used to steal personal information.
 W
WThe Hacker Wars is a 2014 documentary film about hacktivism in the United States, directed by Vivien Lesnik Weisman. It was released on October 17, 2014 in the US.
 W
WHackers in Wonderland is a 2000 documentary film, produced and directed by Russell Barnes, about hackers in the United Kingdom. The documentary contains interviews with the hackers, revealing what drives them to hack, and their opinions about hacktivism.
 W
WHackThisSite.org, commonly referred to as HTS, is an online hacking and security website founded by Jeremy Hammond. The site is maintained by members of the community after his departure. It aims to provide users with a way to learn and practice basic and advanced "hacking" skills through a series of challenges in a safe and legal environment. The organization has a user base of over a million, though the number of active members is believed to be much lower. The most users online at the same time was 19,950 on February 5, 2018 at 2:46:10 AM CST.
 W
WIn Internet activism, hacktivism, or hactivism, is the use of computer-based techniques such as hacking as a form of civil disobedience to promote a political agenda or social change. With roots in hacker culture and hacker ethics, its ends are often related to free speech, human rights, or freedom of information movements.
 W
WAn Internet Protocol camera, or IP camera, is a type of digital video camera that receives control data and sends image data via an IP network. They are commonly used for surveillance but unlike analog closed-circuit television (CCTV) cameras, they require no local recording device, only a local area network. Most IP cameras are webcams, but the term IP camera or netcam usually applies only to those that can be directly accessed over a network connection, usually used for surveillance.
 W
WJonathan Joseph James was an American hacker who was the first juvenile incarcerated for cybercrime in the United States. The South Florida native was 15 years old at the time of the first offense and 16 years old on the date of his sentencing. He died at his Pinecrest, Florida home on May 18, 2008, of a self-inflicted gunshot wound.
 W
WKarl Werner Lothar Koch was a German hacker in the 1980s, who called himself "hagbard", after Hagbard Celine. He was involved in a Cold War computer espionage incident.
 W
WMilw0rm is a group of "hacktivists" best known for penetrating the computers of the Bhabha Atomic Research Centre (BARC) in Mumbai, the primary nuclear research facility of India, on June 3, 1998. The group conducted hacks for political reasons, including the largest mass hack up to that time, inserting an anti-nuclear weapons agenda and peace message on its hacked websites. The group's logo featured the slogan "Putting the power back in the hands of the people."
 W
WThe News International phone-hacking scandal was a controversy involving the now-defunct News of the World and other British newspapers owned by Rupert Murdoch. Employees of the newspaper were accused of engaging in phone hacking, police bribery, and exercising improper influence in the pursuit of stories. Whilst investigations conducted from 2005 to 2007 appeared to show that the paper's phone hacking activities were limited to celebrities, politicians, and members of the British royal family, in July 2011 it was revealed that the phones of murdered schoolgirl Milly Dowler, relatives of deceased British soldiers, and victims of the 7 July 2005 London bombings had also been hacked. The resulting public outcry against News Corporation and its owner Rupert Murdoch led to several high-profile resignations, including that of Murdoch as News Corporation director, Murdoch's son James as executive chairman, Dow Jones chief executive Les Hinton, News International legal manager Tom Crone, and chief executive Rebekah Brooks. The commissioner of London's Metropolitan Police Service (MPS), Sir Paul Stephenson, also resigned. Advertiser boycotts led to the closure of the News of the World on 10 July 2011, after 168 years of publication. Public pressure forced News Corporation to cancel its proposed takeover of the British satellite broadcaster BSkyB.
 W
WOperation Anti-Security, also referred to as Operation AntiSec or #AntiSec, is a series of hacking attacks performed by members of the hacking group LulzSec and Anonymous, and others inspired by the announcement of the operation. LulzSec performed the earliest attacks of the operation, with the first against the Serious Organised Crime Agency on 20 June 2011. Soon after, the group released information taken from the servers of the Arizona Department of Public Safety; Anonymous would later release information from the same agency two more times. An offshoot of the group calling themselves LulzSecBrazil launched attacks on numerous websites belonging to the Government of Brazil and the energy company Petrobras. LulzSec claimed to retire as a group, but on 18 July they reconvened to hack into the websites of British newspapers The Sun and The Times, posting a fake news story of the death of the publication's owner Rupert Murdoch.
 W
WRobin Sage is a fictional American cyber threat analyst. She was created in December 2009 by Robin Casey and Thomas Ryan, two controversial security specialists and white hat hackers from New York City. Her name was taken from a training exercise of United States Army Special Forces.
 W
WRoman Valerevich Seleznev, also known by his hacker name Track2, is a Russian computer hacker. Seleznev was indicted in the United States in 2011, and was convicted of hacking into servers to steal credit-card data. His activities are estimated to have caused more than $169 million in damages to businesses and financial institutions. Seleznev was arrested on July 5, 2014, and was sentenced to 27 years in prison for wire fraud, intentional damage to a protected computer, and identity theft.
 W
WIn computer security, a vulnerability is a weakness which can be exploited by a threat actor, such as an attacker, to cross privilege boundaries within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerabilities are also known as the attack surface.
 W
WA web shell is a shell-like interface that enables a web server to be remotely accessed, often for the purposes of cyberattacks. A web shell is unique in that a web browser is used to interact with it.