 W
WA cryptanalytic computer is a computer designed to be used for cryptanalysis, which nowadays involves massive statistical analysis and multiple trial decryptions that since before World War II are possible only with automated equipment. Polish cryptanalysts designed and built automated aids in their work on Enigma traffic. Arguably, the first modern computer was built for cryptanalytic work at Bletchley Park during the war. More modern computers were important after World War II, and some machines are reported to have had machine instructions hardwired in at the request of NSA.
 W
WCrypto1 is a proprietary encryption algorithm and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless smart cards launched in 1994. Such cards have been used in many notable systems, including Oyster card, CharlieCard and OV-chipkaart.
 W
WCrypto: How the Code Rebels Beat the Government Saving Privacy in the Digital Age is a book about cryptography written by Steven Levy, published in 2001. Levy details the emergence of public key cryptography, digital signatures and the struggle between the National Security Agency (NSA) and the "cypherpunks". The book details the creation of Data Encryption Standard (DES), RSA and the Clipper chip.
 W
WThe Cryptographic Module Validation Program (CMVP) is a joint American and Canadian security accreditation program for cryptographic modules. The program is available to any vendors who seek to have their products certified for use by the U.S. Government and regulated industries that collect, store, transfer, share and disseminate "sensitive, but not classified" information. All of the tests under the CMVP are handled by third-party laboratories that are accredited as Cryptographic Module Testing Laboratories by the National Voluntary Laboratory Accreditation Program (NVLAP). Product certifications under the CMVP are performed in accordance with the requirements of FIPS 140-2.
 W
WIn cryptography, DEAL is a symmetric block cipher derived from the Data Encryption Standard (DES). The design was proposed in a report by Lars Knudsen in 1998, and was submitted to the AES contest by Richard Outerbridge.
 W
WEnigmail is a data encryption and decryption extension for Mozilla Thunderbird and the Postbox that provides OpenPGP public key e-mail encryption and signing. Enigmail works under Microsoft Windows, Unix-like, and Mac OS X operating systems. Enigmail can operate with other mail clients compatible with PGP/MIME and inline PGP such as: Microsoft Outlook with Gpg4win package installed, Gnome Evolution, KMail, Claws Mail, Gnus, Mutt. Its cryptographic functionality is handled by GNU Privacy Guard.
 W
WEnRUPT is a block cipher and a family of cryptographic algorithms based on XXTEA. EnRUPT hash function was submitted to SHA-3 competition but it wasn't selected to the second round.
 W
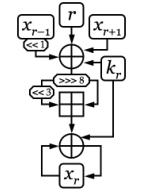
WThe HX-63 was an advanced rotor machine designed by Crypto AG, who started the design in 1952. The machine had nine rotors, each with 41 contacts. There were 26 keyboard inputs and outputs, leaving 15 wires to "loop back" through the rotors via a different path. Moreover, each rotor wire could be selected from one of two paths. The movement of the rotors was irregular and controlled by switches. There were two plugboards with the machine; one to scramble the input, and one for the loop-back wires. The machine could be set up in around 10600 different configurations.
 W
WThe IBM 4758 PCI Cryptographic Coprocessor is a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCI board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed.
 W
WIn cryptography, the IDEA NXT algorithm is a block cipher designed by Pascal Junod and Serge Vaudenay of EPFL. It was conceived between 2001 and 2003. The project was originally named FOX and was published in 2003. In May 2005 it was announced by MediaCrypt under the name IDEA NXT. IDEA NXT is the successor to the International Data Encryption Algorithm (IDEA) and also uses the Lai–Massey scheme. MediaCrypt AG holds patents on elements of IDEA and IDEA NXT. The cipher is specified in two configurations: NXT64 and NXT128.
 W
WJADE was the codename given by US codebreakers to a Japanese World War II cipher machine. The Imperial Japanese Navy used the machine for communications from late 1942 until 1944. JADE was similar to another cipher machine, CORAL, with the main difference that JADE was used to encipher messages in katakana using an alphabet of 50 symbols.
 W
WIn public-key cryptography, a key signing party is an event at which people present their public keys to others in person, who, if they are confident the key actually belongs to the person who claims it, digitally sign the certificate containing that public key and the person's name, etc. Key signing parties are common within the PGP and GNU Privacy Guard community, as the PGP public key infrastructure does not depend on a central key certifying authority, but to a distributed web of trust approach. Key signing parties are a way to strengthen the web of trust. Participants at a key signing party are expected to present adequate identity documents.
 W
WThe KL-43 is a portable, electronic cipher device used by the United States and the NATO from the early 1980s. The machine, manufactured by TRW, is an adaptation of language translator technology, and includes a keyboard for input and an LCD for output. It also contains a built-in modem, a telephone coupler, and the facility for connecting to a printer. A version of the KL-43 was famously used by Oliver North to communicate with his assistant, Fawn Hall, and others while managing clandestine operations in Nicaragua in support of the "Contra" rebels. The device was paraded in front of cameras during the Iran-Contra congressional hearings.
 W
WThe KL-51 is an off-line keyboard encryption system that read and punched paper tape for use with teleprinters. In NATO it was called RACE.
 W
WThe KOI-18 is a hand-held paper tape reader developed by the U.S. National Security Agency as a fill device for loading cryptographic keys, or "crypto variables," into security devices, such as encryption systems. It can read 8-level paper or PET tape, which is manually pulled through the reader slot by the operator. It is battery powered and has no internal storage, so it can load keys of different lengths, including the 128-bit keys used by more modern systems. The KOI-18 can also be used to load keys into other fill devices that do have internal storage, such as the KYK-13 and AN/CYZ-10. The KOI-18 only supports the DS-102 interface.
 W
WKryptographik Lehrbuch der Geheimschreibekunst is an 1809 book on cryptography written by Johann Ludwig Klüber.
 W
WThe Speech Security Equipment (VINSON), TSEC/KY-57, is a portable, tactical cryptographic device in the VINSON family, designed to provide voice encryption for a range of military communication devices such as radio or telephone.
 W
WThe VINSON KY-58 is a secure voice module primarily used to encrypt radio communication to and from military aircraft and other tactical vehicles. It is employed by U.S. Military Joint Services, NATO and some law enforcement agencies. It is designed to operate over bandwidth-restricted circuits such as UHF and VHF satellite access and wideband switched telephone systems. It uses the 16 kbit/s continuously variable slope delta modulation (CVSD). The system was initially fielded as a replacement for the KG-36 and KG-34. The unit fits in a five-inch cube and weighs about 5 pounds. Production ended in 1993.
 W
WTSEC/KY-68 DSVT, commonly known as Digital Subscriber Voice Terminal, is a US military ruggedized, full- or half-duplex tactical telephone system with a built-in encryption/decryption module for secure traffic.
 W
WLEVIATHAN is a stream cipher submitted to NESSIE by Scott Fluhrer and David McGrew. It is a seekable stream cipher, which means that the user may efficiently skip forward to any part of the keystream, much like CTR mode or Salsa20, but unlike those ciphers generating contiguous blocks of the keystream is made especially efficient by LEVIATHAN's unique tree structure based stream generation. LEVIATHAN achieves around 11 cycles per byte on a Pentium II processor.
 W
WThe Navajo I is a secure telephone built into a briefcase that was developed by the U.S. National Security Agency. According to information on display in 2002 at the NSA's National Cryptologic Museum, 110 units were built in the 1980s for use by senior government officials when traveling. It uses the linear predictive coding algorithm LPC-10 at 2.4 kilobits/second.
 W
WNESTOR was a family of compatible, tactical, wideband secure voice systems developed by the U.S. National Security Agency and widely deployed during the Vietnam War through the late Cold War period of the 1980s. NESTOR consists of three systems. The KY-8 was used in vehicular and afloat applications; the KY-28 was the airborne version: and the KY-38 was the portable or man-pack model. About 30,000 NESTOR equipments were produced prior to their replacement by the VINSON secure voice family.
 W
WNoreen, or BID 590, was an off-line one-time tape cipher machine of British origin.
 W
WIn cryptography, a permutation box is a method of bit-shuffling used to permute or transpose bits across S-boxes inputs, retaining diffusion while transposing.
 W
WIn cryptography, a pinwheel was a device for producing a short pseudorandom sequence of bits, as a component in a cipher machine. A pinwheel consisted of a rotating wheel with a certain number of positions on its periphery. Each position had a "pin", "cam" or "lug" which could be either "set" or "unset". As the wheel rotated, each of these pins would in turn affect other parts of the machine, producing a series of "on" or "off" pulses which would repeat after one full rotation of the wheel. If the machine contained more than one wheel, usually their periods would be relatively prime to maximize the combined period. Pinwheels might be turned through a purely mechanical action or electromechanically.
 W
WPortex was a British cipher machine. A rotor machine, the device used eight rotors each with a tyre ring and an insert. The machine was used mainly by the secret services from the late 1940s to the early 1950s.
 W
WA reflector, in cryptology, is a component of some rotor cipher machines, such as the Enigma machine, that sends electrical impulses that have reached it from the machine's rotors, back in reverse order through those rotors. The reflector simplified using the same machine setup for encryption and decryption, but it creates a weakness in the encryption: with a reflector the encrypted version of a given letter can never be that letter itself. That limitation aided World War II code breakers in cracking Enigma encryption. The comparable WW II U.S. cipher machine, SIGABA, did not include a reflector.
 W
WThe Riverbank Publications are a series of pamphlets written by the people who worked for millionaire George Fabyan in the multi-discipline research facility he built in the early 20th century near Chicago. They were published by Fabyan, often without author credit. The publications on cryptanalysis, mostly written by William Friedman, with contributions from Elizebeth Smith Friedman and others, are considered seminal in the field. In particular, Publication 22 introduced the Index of Coincidence, a powerful statistical tool for cryptanalysis.
 W
WRockex, or Telekrypton, was an offline one-time tape Vernam cipher machine known to have been used by Britain and Canada from 1943. It was developed by Canadian electrical engineer Benjamin deForest Bayly, working during the war for British Security Coordination.
A Secure Access Module is based on SmartCard Integrated circuits and is used to enhance the security and cryptography performance in devices, commonly in devices needing to perform secure transactions, such as payment terminals. It can be used for cryptographic computation and secure authentication against smart cards or contactless EMV cards.
 W
WSecure Communication based on Quantum Cryptography (SECOQC) is a project that aims to develop quantum cryptography. The European Union decided in 2004 to invest 11 million EUR in the project as a way of circumventing espionage attempts by ECHELON. Christian Monyk, the coordinator of SECOQC, said people and organizations in Austria, Belgium, the United Kingdom, Canada, the Czech Republic, Denmark, France, Germany, Italy, Russia, Sweden, and Switzerland would participate in the project.
 W
WSIGTOT was a one-time tape machine for encrypting teleprinter communication that was used by the United States during World War II and after for the most sensitive message traffic. It was developed after security flaws were discover in an earlier rotor machine for the same purpose, called SIGCUM. SIGTOT was designed by Leo Rosen and used the same Bell Telephone 132B2 mixer as SIGCUM. The British developed a similar machine called the 5-UCO. Later an improved mixer, the SSM-33, replaced the 131B2,
 W
WDouglas Robert Stinson is a Canadian mathematician and cryptographer, currently a Professor Emeritus at the University of Waterloo.
 W
WThe STU-I, like its successors sometimes known as a "stew phone", was a secure telephone developed by the U.S. National Security Agency for use by senior U.S. government officials in the 1970s.
 W
WSubject Alternative Name (SAN) is an extension to X.509 that allows various values to be associated with a security certificate using a subjectAltName field. These values are called Subject Alternative Names (SANs). Names include:Email addresses IP addresses URIs DNS names: this is usually also provided as the Common Name RDN within the Subject field of the main certificate. Directory names: alternative Distinguished Names to that given in the Subject. Other names, given as a General Name or Universal Principal Name: a registered object identifier followed by a value.
 W
WThe U-229 is a cable connector currently used by the U.S. military for audio connections to field radios, typically for connecting a handset. There are five-pin and six-pin versions, the sixth pin version using the extra pin to power accessories. This type of connector is also used by the National Security Agency to load cryptographic keys into encryption equipment from a fill device.
 W
WA U-Key is an implementation of the MIFARE RFID chip, encased in a plastic key style housing. It is used as a prepayment system on vending machines and for some self-service diving air compressors in Switzerland
 W
WThe xor–encrypt–xor (XEX) is a (tweakable) mode of operation of a block cipher.XEX-based tweaked-codebook mode with ciphertext stealing is one of the more popular modes of operation for whole-disk encryption. XEX is a common form of key whitening. XEX is part of some smart card proposals.