 W
WComputer security software or cybersecurity software is any computer program designed to influence information security. This is often taken in the context of defending computer systems or data, yet can incorporate programs designed specifically for subverting computer systems due to their significant overlap, and the adage that the best defense is a good offense.
 W
WArmitage is a graphical cyber attack management tool for the Metasploit Project that visualizes targets and recommends exploits. It is a free and open source network security tool notable for its contributions to red team collaboration allowing for: shared sessions, data, and communication through a single Metasploit instance. Armitage is written and supported by Raphael Mudge.
 W
WArpON is a computer software project to improve network security. It has attracted interest among network managers and academic researchers and is frequently cited as a means of protecting against ARP-based attacks.
 W
WAvast Software s.r.o. is a Czech multinational cybersecurity software company headquartered in Prague, Czech Republic that researches and develops computer security software, machine learning and artificial intelligence. Avast has more than 435 million monthly active users and the second largest market share among anti-malware application vendors worldwide as of April 2020. The company has approximately 1,700 employees across its 25 offices worldwide. In August 2021, the company's board agreed an offer from NortonLifeLock to acquire the company for US$8 billion.
 W
WCheckmarx is a global software security company headquartered in Ramat Gan, Israel. Founded in 2006, Checkmarx integrates automated software security technologies into DevOps. Checkmarx provides static and interactive application security testing, software composition analysis (SCA), infrastructure as code security testing (KICS), and application security and training development (Codebashing).
 W
Wchkrootkit is a common Unix-based program intended to help system administrators check their system for known rootkits. It is a shell script using common UNIX/Linux tools like the strings and grep commands to search core system programs for signatures and for comparing a traversal of the /proc filesystem with the output of the ps command to look for discrepancies.
 W
WCosign is an open-source project originally designed by the Research Systems Unix Group to provide the University of Michigan with a secure single sign-on web authentication system.
 W
WESET NOD32 Antivirus, commonly known as NOD32, is an antivirus software package made by the Slovak company ESET. ESET NOD32 Antivirus is sold in two editions, Home Edition and Business Edition. The Business Edition packages add ESET Remote Administrator allowing for server deployment and management, mirroring of threat signature database updates and the ability to install on Microsoft Windows Server operating systems.
 W
WFail2Ban is an intrusion prevention software framework that protects computer servers from brute-force attacks. Written in the Python programming language, it is able to run on POSIX systems that have an interface to a packet-control system or firewall installed locally, for example, iptables or TCP Wrapper.
 W
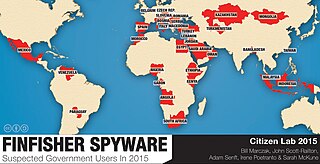
WFinFisher, also known as FinSpy, is surveillance software marketed by Lench IT Solutions plc, which markets the spyware through law enforcement channels.
 W
WAndroid Runtime for Chrome (ARC) is a compatibility layer and sandboxing technology for running Android applications on desktop and laptop computers in an isolated environment. It allows applications to be safely run from a web browser, independent of user operating system, at near-native speeds.
 W
WIn computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data that appears to be a legitimate part of the site and contain information or resources of value to attackers. It is actually isolated, monitored, and capable of blocking or analyzing the attackers. This is similar to police sting operations, colloquially known as "baiting" a suspect.
 W
W W
WHMA is a VPN service founded in 2005 in the United Kingdom. It has been a subsidiary of the Czech cybersecurity company Avast since 2016.
 W
WThe idle scan is a TCP port scan method that consists of sending spoofed packets to a computer to find out what services are available. This is accomplished by impersonating another computer whose network traffic is very slow or nonexistent. This could be an idle computer, called a "zombie".
 W
WIObit Malware Fighter is an anti-malware and anti-virus program for the Microsoft Windows operating system. It is designed to remove and protect against malware, including, but not limited to: Trojans, rootkits, and ransomware.
 W
WKaspersky Lab is a Russian multinational cybersecurity and anti-virus provider headquartered in Moscow, Russia and operated by a holding company in the United Kingdom. It was founded in 1997 by Eugene Kaspersky, Natalya Kaspersky, and Alexey De-Monderik; Eugene Kaspersky is currently the CEO. Kaspersky Lab develops and sells antivirus, internet security, password management, endpoint security, and other cybersecurity products and services.
 W
WMISP Threat Sharing (MISP) is an open source threat intelligence platform. The project develops utilities and documentation for more effective threat intelligence, by sharing indicators of compromise. There are several organizations who run MISP instances, who are listed on the website.
 W
WMicrosoft Forefront Threat Management Gateway, formerly known as Microsoft Internet Security and Acceleration Server, is a network router, firewall, antivirus program, VPN server and web cache from Microsoft Corporation. It runs on Windows Server and works by inspecting all network traffic that passes through it.
 W
WNetwork Security Toolkit (NST) is a Linux-based Live DVD/USB Flash Drive that provides a set of free and open-source computer security and networking tools to perform routine security and networking diagnostic and monitoring tasks. The distribution can be used as a network security analysis, validation and monitoring tool on servers hosting virtual machines. The majority of tools published in the article "Top 125 security tools" by Insecure.org are available in the toolkit. NST has package management capabilities similar to Fedora and maintains its own repository of additional packages.
 W
WNikto is a free software command-line vulnerability scanner that scans webservers for dangerous files/CGIs, outdated server software and other problems. It performs generic and server type specific checks. It also captures and prints any cookies received. The Nikto code itself is free software, but the data files it uses to drive the program are not. Version 1.00 was released December 27, 2001.
 W
WOpenPuff Steganography and Watermarking, sometimes abbreviated OpenPuff or Puff, is a free steganography tool for Microsoft Windows created by Cosimo Oliboni and still maintained as independent software. The program is notable for being the first steganography tool that:lets users hide data in more than a single carrier file. When hidden data are split among a set of carrier files you get a carrier chain, with no enforced hidden data theoretical size limit implements 3 layers of hidden data obfuscation extends deniable cryptography into deniable steganography
 W
WPacket Sender is an open source utility to allow sending and receiving TCP and UDP packets. It also supports TCP connections using SSL. It is available for Windows, Mac, and Linux. It is licensed GNU General Public License v2 and is free software. Packet Sender's web site says "It's designed to be very easy to use while still providing enough features for power users to do what they need.".
Paramount Defenses is a privately held American Cyber Security company that develops cyber security solutions to "help organizations secure their foundational Microsoft Active Directory deployments".
 W
WParrot OS is a Linux distribution based on Debian with a focus on security, privacy, and development.
 W
WprivacyIDEA is a Two Factor Authentication System which is multi-tenency- and multi-instance-capable. It is opensource, written in Python and hosted at GitHub.
 W
WA proxy list is a list of open HTTP/HTTPS/SOCKS proxy servers all on one website. Proxies allow users to make indirect network connections to other computer network services. Proxy lists include the IP addresses of computers hosting open proxy servers, meaning that these proxy servers are available to anyone on the internet. Proxy lists are often organized by the various proxy protocols the servers use. Many proxy lists index Web proxies, which can be used without changing browser settings.
 W
WIn computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
 W
Wrkhunter is a Unix-based tool that scans for rootkits, backdoors and possible local exploits. It does this by comparing SHA-1 hashes of important files with known good ones in online databases, searching for default directories, wrong permissions, hidden files, suspicious strings in kernel modules, and special tests for Linux and FreeBSD. rkhunter is notable due to its inclusion in popular operating systems
 W
WSaferSurf is a software product for anonymous internet surfing. Aside from offering web anonymity, it has several other features, such as a geolocation proxy service bypassing country restrictions. SaferSurf runs centrally on a server and doesn't need a local installation.
 W
WScapy is a packet manipulation tool for computer networks, originally written in Python by Philippe Biondi. It can forge or decode packets, send them on the wire, capture them, and match requests and replies. It can also handle tasks like scanning, tracerouting, probing, unit tests, attacks, and network discovery.
 W
WSendmail, Inc. is an email management business.
 W
WSnare is a collection of software tools that collect audit log data from a variety of operating systems and applications to facilitate centralised log analysis. Enterprise Agents are available for Linux, macOS, Windows, Solaris, Microsoft SQL Server, a variety of browsers, and more. Snare Enterprise Epilog for Windows facilitates the central collection and processing of Windows text-based log files such as ISA/IIS. Snare Enterprise Epilog for Unix provides a method to collect any text based log files on the Linux and Solaris operating systems. Opensource Agents are available for Irix and AIX.
 W
WSnort is a free open source network intrusion detection system (IDS) and intrusion prevention system (IPS) created in 1998 by Martin Roesch, founder and former CTO of Sourcefire. Snort is now developed by Cisco, which purchased Sourcefire in 2013.
 W
Wsudo is a program for Unix-like computer operating systems that allows users to run programs with the security privileges of another user, by default the superuser. It originally stood for "superuser do" as the older versions of sudo were designed to run commands only as the superuser. However, the later versions added support for running commands not only as the superuser but also as other (restricted) users, and thus it is also commonly expanded as "substitute user do". Although the latter case reflects its current functionality more accurately, sudo is still often called "superuser do" since it is so often used for administrative tasks.
 W
WSuricata is an open source-based intrusion detection system (IDS) and intrusion prevention system (IPS). It was developed by the Open Information Security Foundation (OISF). A beta version was released in December 2009, with the first standard release following in July 2010.
 W
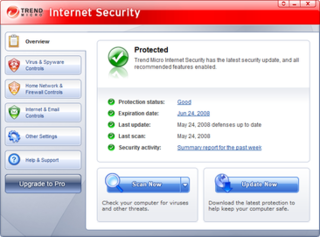
WTrend Micro Internet Security is an antivirus and online security program developed by Trend Micro for the consumer market. According to NSS Lab comparative analysis of software products for this market in 2014, Trend Micro Internet Security was fastest in responding to new internet threats.
 W
WUSBKill is anti-forensic software distributed via GitHub, written in Python for the BSD, Linux, and OS X operating systems. It is designed to serve as a kill switch if the computer on which it is installed should fall under the control of individuals or entities against the desires of the owner. It is free software, available under the GNU General Public License.
 W
WA vulnerability scanner is a computer program designed to assess computers, networks or applications for known weaknesses. These scanners are used to discover the weaknesses of a given system. They are utilized in the identification and detection of vulnerabilities arising from mis-configurations or flawed programming within a network-based asset such as a firewall, router, web server, application server, etc. Modern vulnerability scanners allow for both authenticated and unauthenticated scans. Modern scanners are typically available as SaaS ; provided over the internet and delivered as a web application. The modern vulnerability scanner often has the ability to customize vulnerability reports as well as the installed software, open ports, certificates and other host information that can be queried as part of its workflow.Authenticated scans allow for the scanner to directly access network based assets using remote administrative protocols such as secure shell (SSH) or remote desktop protocol (RDP) and authenticate using provided system credentials. This allows the vulnerability scanner to access low-level data, such as specific services and configuration details of the host operating system. It's then able to provide detailed and accurate information about the operating system and installed software, including configuration issues and missing security patches. Unauthenticated scans is a method that can result in a high number of false positives and is unable to provide detailed information about the assets operating system and installed software. This method is typically used by threat actors or security analyst trying determine the security posture of externally accessible assets.
 W
Ww3af is an open-source web application security scanner. The project provides a vulnerability scanner and exploitation tool for Web applications. It provides information about security vulnerabilities for use in penetration testing engagements. The scanner offers a graphical user interface and a command-line interface.
 W
WWindows Live OneCare Safety Scanner was an online scanning, PC cleanup, and diagnosis service to help remove of viruses, spyware/adware, and other malware. It was a free web service that was part of Windows Live.
 W
WIn computing, Winlogon is the component of Microsoft Windows operating systems that is responsible for handling the secure attention sequence, loading the user profile on logon, and optionally locking the computer when a screensaver is running. The actual obtainment and verification of user credentials is left to other components. Winlogon is a common target for several threats that could modify its function and memory usage. Increased memory usage for this process might indicate that it has been "hijacked". In Windows Vista and later operating systems, Winlogon's roles and responsibilities have changed significantly.
 W
WWOT Services is the developer of MyWOT, an online reputation and Internet safety service which shows indicators of trust about existing websites. The confidence level is based both on user ratings and on third-party malware, phishing, scam and spam blacklists. The service also provides crowdsourced reviews, about to what extent websites are trustworthy, and respect user privacy, vendor reliability and child safety.