 W
WIn mathematics and computer science, an algorithm is a finite sequence of well-defined, computer-implementable instructions, typically to solve a class of problems or to perform a computation. Algorithms are always unambiguous and are used as specifications for performing calculations, data processing, automated reasoning, and other tasks.
 W
WCoded exposure photography, also known as a flutter shutter, is the name given to any mathematical algorithm that reduces the effects of motion blur in photography. The key element of the coded exposure process is the mathematical formula that affects the shutter frequency. This involves the calculation of the relationship between the photon exposure of the light sensor and the randomized code. The camera is made to take a series of snapshots with random time intervals using a simple computer, this creates a blurred image that can be reconciled into a clear image using the algorithm.
 W
WAlgorism is the technique of performing basic arithmetic by writing numbers in place value form and applying a set of memorized rules and facts to the digits. One who practices algorism is known as an algorist. This positional notation system largely superseded earlier calculation systems that used a different set of symbols for each numerical magnitude, such as Roman numerals, and in some cases required a device such as an abacus.
 W
WAlgorithms of Oppression: How Search Engines Reinforce Racism is a 2018 book by Safiya Umoja Noble in the fields of information science, machine learning, and human-computer interaction.
 W
WAutomate This: How Algorithms Came to Rule Our World is a book written by Christopher Steiner and published by Penguin Group. Steiner begins his study of algorithms on Wall Street in the 1980s but also provides examples from other industries. For example, he explains the history of Pandora Radio and the use of algorithms in music identification. He expresses concern that such use of algorithms may lead to the homogenization of music over time. Steiner also discusses the algorithms that eLoyalty was created by dissecting 2 million speech patterns and can now identify a caller's personality style and direct the caller with a compatible customer support representative.
 W
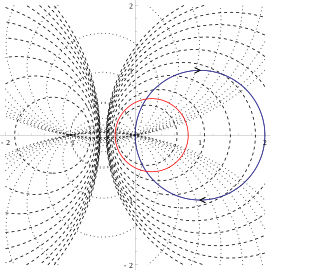
WHall circles are a graphical tool in control theory used to obtain values of a closed-loop transfer function from the Nyquist plot of the associated open-loop transfer function. Hall circles have been introduced in control theory by Albert C. Hall in his thesis.
 W
WThe Kinetic Simulation Algorithm Ontology (KiSAO) supplies information about existing algorithms available for the simulation of systems biology models, their characterization and interrelationships. KiSAO is part of the BioModels.net project and of the COMBINE initiative.
 W
WBürgi's Kunstweg is a set of algorithms invented by Jost Bürgi at the end of the 16th century. They can be used for the calculation of sines to an arbitrary precision. Bürgi used these algorithms to calculate a Canon Sinuum, a table of sines in steps of 2 arc seconds. It is thought that this table had 8 sexagesimal places. Some authors have speculated that this table only covered the range from 0 to 45 degrees, but nothing seems to support this claim. Such tables were extremely important for navigation at sea. Johannes Kepler called the Canon Sinuum the most precise known table of sines. Bürgi explained his algorithms in his work Fundamentum Astronomiae which he presented to Emperor Rudolf II. in 1592.
 W
WLancichinetti–Fortunato–Radicchi benchmark is an algorithm that generates benchmark networks. They have a priori known communities and are used to compare different community detection methods. The advantage of the benchmark over other methods is that it accounts for the heterogeneity in the distributions of node degrees and of community sizes.
 W
WThere are many programs and algorithms used to plot the Mandelbrot set and other fractals, some of which are described in fractal-generating software. These programs use a variety of algorithms to determine the color of individual pixels efficiently.
 W
WThe Master Algorithm: How the Quest for the Ultimate Learning Machine Will Remake Our World is a book by Pedro Domingos released in 2015. Domingos wrote the book in order to generate interest from people outside the field.
 W
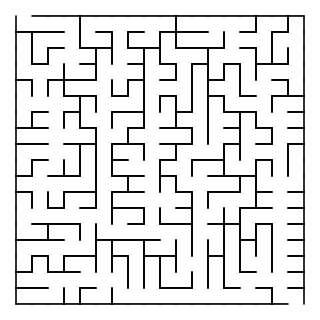
WMaze generation algorithms are automated methods for the creation of mazes.
 W
WThere are a number of different maze solving algorithms, that is, automated methods for the solving of mazes. The random mouse, wall follower, Pledge, and Trémaux's algorithms are designed to be used inside the maze by a traveler with no prior knowledge of the maze, whereas the dead-end filling and shortest path algorithms are designed to be used by a person or computer program that can see the whole maze at once.
 W
WA medical algorithm is any computation, formula, statistical survey, nomogram, or look-up table, useful in healthcare. Medical algorithms include decision tree approaches to healthcare treatment and also less clear-cut tools aimed at reducing or defining uncertainty. A medical prescription is also a type of medical algorithm.
 W
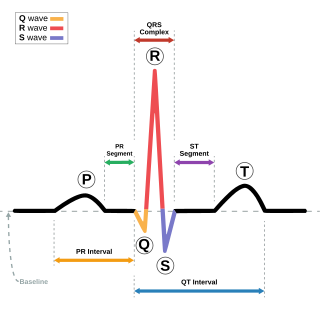
WThe Pan–Tompkins algorithm is commonly used to detect QRS complexes in electrocardiographic signals (ECG). The QRS complex represents the ventricular depolarization and the main spike visible in an ECG signal. This feature makes it particularly suitable for measuring heart rate, the first way to assess the heart health state. In the first derivation of Einthoven of a physiological heart, the QRS complex is composed by a downward deflection, a high upward deflection and a final downward deflection.
 W
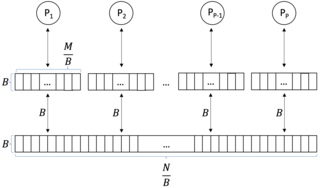
WIn computer science, a parallel external memory (PEM) model is a cache-aware, external-memory abstract machine. It is the parallel-computing analogy to the single-processor external memory (EM) model. In a similar way, it is the cache-aware analogy to the parallel random-access machine (PRAM). The PEM model consists of a number of processors, together with their respective private caches and a shared main memory.
 W
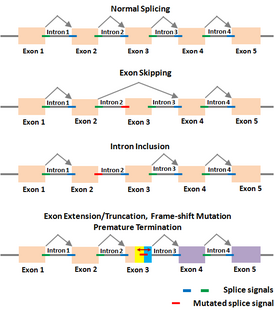
WThe Shapiro–Senapathy algorithm (S&S) is an algorithm for predicting the splice sites, exons and genes in animals and plants. This algorithm has the ability to discover disease-causing mutations in splice junctions in cancerous and non-cancerous diseases that is being used in major research institutions around the world.
 W
WShuffling is a procedure used to randomize a deck of playing cards to provide an element of chance in card games. Shuffling is often followed by a cut, to help ensure that the shuffler has not manipulated the outcome.
 W
WIn mathematics, the sieve of Eratosthenes is an ancient algorithm for finding all prime numbers up to any given limit.
 W
WIn computer programming, the XOR swap is an algorithm that uses the XOR bitwise operation to swap values of distinct variables having the same data type without using a temporary variable. "Distinct" means that the variables are stored at different, non-overlapping, memory addresses as the algorithm would set a single aliased value to zero; the actual values of the variables do not have to be different.