 W
WThe Combined Cipher Machine (CCM) was a common cipher machine system for securing Allied communications during World War II and, for a few years after, by NATO. The British Typex machine and the US ECM Mark II were both modified so that they were interoperable.
 W
WCreed & Company was a British telecommunications company founded by Frederick George Creed which was an important pioneer in the field of teleprinter machines. It was merged into the International Telephone and Telegraph Corporation (ITT) in 1928.
 W
WThe word cryptex is a neologism coined by the author Dan Brown for his 2003 novel The Da Vinci Code, denoting a portable vault used to hide secret messages. It is a word formed from Greek κρυπτός kryptós, "hidden, secret" and Latin codex; "an apt title for this device" since it uses "the science of cryptology to protect information written on the contained scroll or codex". The first physical cryptex was created by Justin Kirk Nevins in 2004.
 W
WIn computing, a cryptographic accelerator is a co-processor designed specifically to perform computationally intensive cryptographic operations, doing so far more efficiently than the general-purpose CPU. Because many servers' system load consists mostly of cryptographic operations, this can greatly increase performance.
 W
WIn cryptography, the EFF DES cracker is a machine built by the Electronic Frontier Foundation (EFF) in 1998, to perform a brute force search of the Data Encryption Standard (DES) cipher's key space – that is, to decrypt an encrypted message by trying every possible key. The aim in doing this was to prove that the key size of DES was not sufficient to be secure.
 W
WThe Enigma machine is an encryption device developed and used in the early- to mid-20th century to protect commercial, diplomatic and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military. Germany's use of the Enigma machine gave them the unique ability to communicate securely and a huge advantage in World War II. The Enigma machine was considered to be so secure that even the most top secret messages were sent via its electrical circuits.
 W
WIn cryptography, Fialka (M-125) is the name of a Cold War-era Soviet cipher machine. A rotor machine, the device uses 10 rotors, each with 30 contacts along with mechanical pins to control stepping. It also makes use of a punched card mechanism. Fialka means "violet" in Russian. Information regarding the machine was quite scarce until c. 2005 because the device had been kept secret.
 W
WFish was the UK's GC&CS Bletchley Park codename for any of several German teleprinter stream ciphers used during World War II. Enciphered teleprinter traffic was used between German High Command and Army Group commanders in the field, so its intelligence value (Ultra) was of the highest strategic value to the Allies. This traffic normally passed over landlines, but as German forces extended their geographic reach beyond western Europe, they had to resort to wireless transmission.
 W
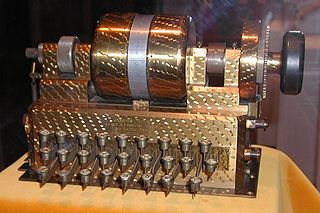
WThe Hebern Rotor Machine was an electro-mechanical encryption machine built by combining the mechanical parts of a standard typewriter with the electrical parts of an electric typewriter, connecting the two through a scrambler. It is the first example of a class of machines known as rotor machines that would become the primary form of encryption during World War II and for some time after, and which included such famous examples as the German Enigma.
 W
WThe IBM 4758 PCI Cryptographic Coprocessor is a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCI board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed.
 W
WThe Lorenz SZ40, SZ42a and SZ42b were German rotor stream cipher machines used by the German Army during World War II. They were developed by C. Lorenz AG in Berlin. The model name SZ was derived from Schlüssel-Zusatz, meaning cipher attachment. The instruments implemented a Vernam stream cipher.
 W
WThe M-94 was a piece of cryptographic equipment used by the United States army, consisting of several lettered discs arranged as a cylinder. It was also employed by the US Navy, under the name CSP 488.
 W
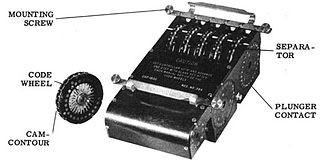
WIn cryptography, the M-209, designated CSP-1500 by the United States Navy is a portable, mechanical cipher machine used by the US military primarily in World War II, though it remained in active use through the Korean War. The M-209 was designed by Swedish cryptographer Boris Hagelin in response to a request for such a portable cipher machine, and was an improvement of an earlier machine, the C-36.
 W
WIn the history of cryptography, M-325, also known as SIGFOY, was an American rotor machine designed by William F. Friedman and built in 1944. Between 1944 and 1946, more than 1,100 machines were deployed within the United States Foreign Service. Its use was discontinued in 1946 because of faults in operation. Friedman applied for a patent on the M-325 on 11 August 1944; it wasand was granted on 17 March 1959.
 W
WNoreen, or BID 590, was an off-line one-time tape cipher machine of British origin.
 W
WThe OMI cryptograph was a rotor cipher machine produced and sold by Italian firm Ottico Meccanica Italiana (OMI) in Rome.
 W
WIn cryptography, a pinwheel was a device for producing a short pseudorandom sequence of bits, as a component in a cipher machine. A pinwheel consisted of a rotating wheel with a certain number of positions on its periphery. Each position had a "pin", "cam" or "lug" which could be either "set" or "unset". As the wheel rotated, each of these pins would in turn affect other parts of the machine, producing a series of "on" or "off" pulses which would repeat after one full rotation of the wheel. If the machine contained more than one wheel, usually their periods would be relatively prime to maximize the combined period. Pinwheels might be turned through a purely mechanical action or electromechanically.
 W
WA plugboard or control panel is an array of jacks or sockets into which patch cords can be inserted to complete an electrical circuit. Control panels are sometimes used to direct the operation of unit record equipment, cipher machines, and early computers.
 W
WPortex was a British cipher machine. A rotor machine, the device used eight rotors each with a tyre ring and an insert. The machine was used mainly by the secret services from the late 1940s to the early 1950s.
 W
WThe Schlüsselgerät 41, also known as the SG-41 or Hitler mill, was a rotor cipher machine, first produced in 1941 in Nazi Germany, that was designed as a potential successor for the Enigma machine. It saw limited use by the Abwehr towards the end of World War II.
 W
WA secure cryptoprocessor is a dedicated computer-on-a-chip or microprocessor for carrying out cryptographic operations, embedded in a packaging with multiple physical security measures, which give it a degree of tamper resistance. Unlike cryptographic processors that output decrypted data onto a bus in a secure environment, a secure cryptoprocessor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained.
 W
WA secure telephone is a telephone that provides voice security in the form of end-to-end encryption for the telephone call, and in some cases also the mutual authentication of the call parties, protecting them against a man-in-the-middle attack. Concerns about massive growth of telephone tapping incidents led to growing demand for secure telephones.
 W
WThe Siemens & Halske T52, also known as the Geheimschreiber, or Schlüsselfernschreibmaschine (SFM), was a World War II German cipher machine and teleprinter produced by the electrical engineering firm Siemens & Halske. The instrument and its traffic were codenamed Sturgeon by British cryptanalysts.
 W
WIn the history of cryptography, the ECM Mark II was a cipher machine used by the United States for message encryption from World War II until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the Navy, and a modified Navy version was termed the CSP-2900.
 W
WA subscriber identity module or subscriber identification module (SIM), widely known as a SIM card, is an integrated circuit that is intended to securely store the international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices. It is also possible to store contact information on many SIM cards. SIM cards are always used on GSM phones; for CDMA phones, they are needed only for LTE-capable handsets. SIM cards can also be used in satellite phones, smart watches, computers, or cameras.
 W
WA subscriber identity module or subscriber identification module (SIM), widely known as a SIM card, is an integrated circuit that is intended to securely store the international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices. It is also possible to store contact information on many SIM cards. SIM cards are always used on GSM phones; for CDMA phones, they are needed only for LTE-capable handsets. SIM cards can also be used in satellite phones, smart watches, computers, or cameras.
 W
WTLS acceleration is a method of offloading processor-intensive public-key encryption for Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL) to a hardware accelerator.
 W
WTrusted Platform Module is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys.
 W
WIn the history of cryptography, Typex machines were British cipher machines used from 1937. It was an adaptation of the commercial German Enigma with a number of enhancements that greatly increased its security. The cipher machine was used until the mid-1950s when other more modern military encryption systems came into use.
 W
WThe YubiKey is a hardware authentication device manufactured by Yubico to protect access to computers, networks, and online services that supports one-time passwords, public-key cryptography, and authentication, and the Universal 2nd Factor (U2F) and FIDO2 protocols developed by the FIDO Alliance. It allows users to securely log into their accounts by emitting one-time passwords or using a FIDO-based public/private key pair generated by the device. YubiKey also allows for storing static passwords for use at sites that do not support one-time passwords. Facebook uses YubiKey for employee credentials. Google supports it for both employees and users. Some password managers support YubiKey. Yubico also manufactures the Security Key, a device similar to the YubiKey, but focused on public-key authentication.