 W
WAkancha Srivastava, is the founder of Akancha Srivastava Foundation. The Foundation was formed in 2017. It is an 80G certified, non-profit organization in India that works for the education and empowerment of people by imparting the knowledge of cyber safety via its initiative Akancha Against Harassment.
 W
WAnonymous is a decentralized international activist/hacktivist collective/movement that is widely known for its various cyber attacks against several governments, government institutions and government agencies, corporations, and the Church of Scientology.
 W
WThe Anti Security Movement is a movement opposed to the computer security industry. Antisec is against full disclosure of information relating tosoftware vulnerabilities, exploits, exploitation techniques, hacking tools, attacking public outlets and distribution points of that information. The general thought behind this is that the computer security industry uses full disclosure to profit and develop scare-tactics to convince people into buying their firewalls, anti-virus software and auditing services.
 W
WIdaho National Laboratory ran the Aurora Generator Test in 2007 to demonstrate how a cyberattack could destroy physical components of the electric grid. The experiment used a computer program to rapidly open and close a diesel generator's circuit breakers out of phase from the rest of the grid and cause it to explode. This vulnerability is referred to as the Aurora Vulnerability.
 W
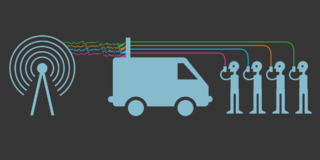
WCellphone surveillance may involve tracking, bugging, monitoring, eavesdropping, and recording conversations and text messages on mobile phones. It also encompasses the monitoring of people's movements, which can be tracked using mobile phone signals when phones are turned on.
 W
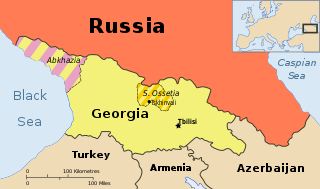
WDuring the Russo-Georgian War a series of cyberattacks swamped and disabled websites of numerous South Ossetian, Georgian, Russian and Azerbaijani organisations. The attacks were initiated three weeks before the shooting war began in what is regarded as "the first case in history of a coordinated cyberspace domain attack synchronized with major combat actions in the other warfighting domains ."
 W
WList of cyberattacks on schools From 2016 to 2019 there have been 855 cyberattacks on U.S. School districts. Microsoft Security Intelligence has said there are more attacks on schools and school districts than any other industry. There were 348 reported cyberattacks on school districts in 2019. School districts are allocating millions of dollars for their computer systems to support virtual learning in the wake of the Covid-19 pandemic. The Miami-Dade Public Schools invested in a $15.3 million online learning system. In 2020 their system was hacked with a Denial of Service Cyber attack.
 W
WCyberBerkut is a modern organized group of pro-Russian hacktivists. The group became locally known for a series of publicity stunts and distributed denial-of-service (DDoS) attacks on Ukrainian government, and western or Ukrainian corporate websites.
 W
WLi Yi Bar is a subforum of the Baidu Tieba forum. This subforum was opened for ridiculing Li Yi. This subforum is well-known for a large number of followers, who often flood other Internet forums or subforums.
 W
WOn 3 September 2020, at 2:53 am EDT, a 16-year-old male from South Miami, Florida was arrested in connection with distributed denial-of-service (DDoS) attacks on the Miami-Dade County Public Schools's computer network, the fourth largest in the US, causing the system to crash during the first three days of the school year. It occurred as the school system was attempting to conduct internet-based instruction during the COVID-19 pandemic of 2020. After monitoring the IP addresses using the network, investigators concluded the teenager and several foreign actors had hacked the system. At the time, the school district had contracted K12 to provide the software necessary for the internet-based instruction. Despite its price tag of $15.3 million, K12 was surprisingly susceptible to the attacks. Consequently, the school district sought the help of the FBI and U.S. Secret Service to investigate.
 W
WMUSCULAR (DS-200B), located in the United Kingdom, is the name of a surveillance program jointly operated by Britain's Government Communications Headquarters (GCHQ) and the U.S. National Security Agency (NSA) that was revealed by documents released by Edward Snowden and interviews with knowledgeable officials. GCHQ is the primary operator of the program. GCHQ and the NSA have secretly broken into the main communications links that connect the data centers of Yahoo! and Google. Substantive information about the program was made public at the end of October 2013.
 W
W"Operation Newscaster", as labelled by American firm iSIGHT Partners in 2014, is a cyber espionage covert operation directed at military and political figures using social networking, allegedly done by Iran. The operation has been described as "creative", "long-term" and "unprecedented". According to iSIGHT Partners, it is "the most elaborate cyber espionage campaign using social engineering that has been uncovered to date from any nation".
 W
WThe Paradise Papers are a set of over 13.4 million confidential electronic documents relating to offshore investments that were leaked to the German reporters Frederik Obermaier and Bastian Obermayer, from the newspaper Süddeutsche Zeitung. The newspaper shared them with the International Consortium of Investigative Journalists, and a network of more than 380 journalists. Some of the details were made public on 5 November 2017 and stories are still being released.
 W
W(Balogh) Petya is a family of encrypting malware that was first discovered in 2016. The malware targets Microsoft Windows–based systems, infecting the master boot record to execute a payload that encrypts a hard drive's file system table and prevents Windows from booting. It subsequently demands that the user make a payment in Bitcoin in order to regain access to the system. The Petya malware had infected millions of people during its first year of its release. The maker of the Petya malware was fined and arrested.
 W
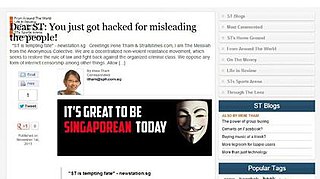
WThe 2013 Singapore cyberattacks were a series of cyberattacks initiated by the hacktivist organisation Anonymous, conducted partly in response to web censorship regulations in Singapore. A member of Anonymous, known by the online handle "The Messiah", claimed responsibility for spearheading the attacks. On 12 November 2013, James Raj was charged in a Singapore court as the alleged "Messiah".
 W
WOn November 24, 2014, a hacker group which identified itself by the name "Guardians of Peace" leaked a release of confidential data from the film studio Sony Pictures. The data included personal information about Sony Pictures employees and their families, e-mails between employees, information about executive salaries at the company, copies of then-unreleased Sony films, plans for future Sony films, scripts for certain films, and other information. The perpetrators then employed a variant of the Shamoon wiper malware to erase Sony's computer infrastructure.
 W
WTitan Rain was a series of coordinated attacks on computer systems in the United States since 2003; they were known to have been ongoing for at least three years. The attacks originated in Guangdong, China. The activity is believed to be associated with a state-sponsored advanced persistent threat. It was given the designation Titan Rain by the federal government of the United States.
 W
WOn July 15, 2020, between 20:00 and 22:00 UTC, reportedly 130 high-profile Twitter accounts were compromised by outside parties to promote a bitcoin scam. Twitter and other media sources confirmed that the perpetrators had gained access to Twitter's administrative tools so that they could alter the accounts themselves and post the tweets directly. They appeared to have used social engineering to gain access to the tools via Twitter employees. Three individuals were arrested by authorities on July 31, 2020 and charged with wire fraud, money laundering, identity theft, and unauthorized computer access related to the scam.
 W
WA series of powerful cyberattacks using the Petya malware began on 27 June 2017 that swamped websites of Ukrainian organizations, including banks, ministries, newspapers and electricity firms. Similar infections were reported in France, Germany, Italy, Poland, Russia, United Kingdom, the United States and Australia. ESET estimated on 28 June 2017 that 80% of all infections were in Ukraine, with Germany second hardest hit with about 9%. On 28 June 2017, the Ukrainian government stated that the attack was halted. On 30 June 2017, the Associated Press reported experts agreed that Petya was masquerading as ransomware, while it was actually designed to cause maximum damage, with Ukraine being the main target.
 W
WThe WannaCry ransomware attack was a May 2017 worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. It propagated through EternalBlue, an exploit discovered by the United States National Security Agency (NSA) for older Windows systems. EternalBlue was stolen and leaked by a group called The Shadow Brokers at least a year prior to the attack. While Microsoft had released patches previously to close the exploit, much of WannaCry's spread was from organizations that had not applied these, or were using older Windows systems that were past their end-of-life. These patches are imperative to an organization's cyber-security but many were not applied because of needing 24/7 operation, risking having applications that used to work break, inconvenience, or other reasons.