 W
WCyberwarfare is the use of digital attacks to attack a nation, causing comparable harm to actual warfare and/or disrupting the vital computer systems. There is significant debate among experts regarding the definition of cyberwarfare, and even if such a thing exists. One view is that the term "cyberwarfare" is a misnomer, since no offensive cyber actions to date could be described as "war". An alternative view is that "cyberwarfare" is a suitable label for cyber attacks which cause physical damage to people and objects in the real world.
 W
WThe 2013 Singapore cyberattacks were a series of cyberattacks initiated by the hacktivist organisation Anonymous, conducted partly in response to web censorship regulations in Singapore. A member of Anonymous, known by the online handle "The Messiah", claimed responsibility for spearheading the attacks. On 12 November 2013, James Raj was charged in a Singapore court as the alleged "Messiah".
 W
WAn advanced persistent threat (APT) is a stealthy threat actor, typically a nation state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period. In recent times, the term may also refer to non-state-sponsored groups conducting large-scale targeted intrusions for specific goals.
 W
WThe Agence nationale de la sécurité des systèmes d'information is a French service created on 7 July 2009 with responsibility for computer security.
 W
WAn application firewall is a form of firewall that controls input/output or system calls of an application or service. It operates by monitoring and blocking communications based on a configured policy, generally with predefined rule sets to choose from. The application firewall can control communications up to the application layer of the OSI model, which is the highest operating layer, and where it gets its name. The two primary categories of application firewalls are network-based and host-based.
 W
WThe Army Signal Command Cybernetic Security Unit is a cyber warfare unit of the Italian Army.
 W
WIdaho National Laboratory ran the Aurora Generator Test in 2007 to demonstrate how a cyberattack could destroy physical components of the electric grid. The experiment used a computer program to rapidly open and close a diesel generator's circuit breakers out of phase from the rest of the grid and cause it to explode. This vulnerability is referred to as the Aurora Vulnerability.
 W
WInternet security awareness or Cyber security awareness refers to how much end-users know about the cyber security threats their networks face, the risks they introduce and mitigating security best practices to guide their behavior. End users are considered the weakest link and the primary vulnerability within a network. Since end-users are a major vulnerability, technical means to improve security are not enough. Organizations could also seek to reduce the risk of the human element. This could be accomplished by providing security best practice guidance for end users' awareness of cyber security. Employees could be taught about common threats and how to avoid or mitigate them.
 W
WA botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "network". The term is usually used with a negative or malicious connotation.
 W
WThe Communications and Information Services Corps (CIS) – formerly the Army Corps of Signals – is one of the combat support corps of the Irish Defence Forces, the military of Ireland. It is responsible for the installation, maintenance and operation of communications and information systems for the command, control and administration of the Defence Forces, and the facilitation of accurate, real-time sharing of intelligence between the Army, Naval Service and Air Corps branches at home and overseas.
 W
WComputer security, cybersecurity, or information technology security is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
 W
WThe Cyber Security Agency of Singapore (CSA) is a government agency of Singapore nominally under the Prime Minister's Office, but is day-to-day administratively managed by the Ministry of Communications and Information (MCI). It provides centralised oversight of national cyber security functions, and works with sector leads to protect Singapore's Critical Information Infrastructure (CII), such as the energy and banking sectors. Formed on 1 April 2015, the agency also engages with various industries and stakeholders to heighten cyber security awareness as well as to ensure the development of Singapore's cyber security. It is headed by the Commissioner of Cybersecurity, David Koh. The Minister-in-charge is Josephine Teo of MCI.
 W
WThe Mongolian Armed Forces is the collective name for the Mongolian military and the joint forces that comprise it. It is tasked with protecting the independence, sovereignty, and territorial integrity of Mongolia. Defined as the peacetime configuration, its current structure consists of five branches: the Mongolian Ground Force, Mongolian Air Force, Construction and Engineering Forces, cyber security, and special forces. In case of a war situation, the Border Troops, Internal Troops and National Emergency Management Agency can be reorganized into the armed forces structure. The General Staff of the Mongolian Armed Forces is the main managing body and operates independently from the Ministry of Defence, its government controlled parent body.
 W
WIT security standards or cyber security standards are techniques generally set forth in published materials that attempt to protect the cyber environment of a user or organization. This environment includes users themselves, networks, devices, all software, processes, information in storage or transit, applications, services, and systems that can be connected directly or indirectly to networks.
 W
WIn computing, a denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
 W
WECHELON, originally a secret government code name, is a surveillance program operated by the United States with the aid of four other signatory states to the UKUSA Security Agreement: Australia, Canada, New Zealand, and the United Kingdom, also known as the Five Eyes.
 W
WEndgame provides a cyber operations platform supporting the detection, exploitation, and mitigation of cyber-threats. Endgame was started by executives from ISS.
 W
WAn evil maid attack is an attack on an unattended device, in which an attacker with physical access alters it in some undetectable way so that they can later access the device, or the data on it.
 W
WFifth-generation warfare (5GW) is warfare that is conducted primarily through non-kinetic military action, such as social engineering, misinformation, cyberattacks, along with emerging technologies such as artificial intelligence and fully autonomous systems. Fifth generation warfare has been described by Daniel Abbot as a war of "information and perception". There is no widely agreed upon definition of fifth-generation warfare, and it has been rejected by some scholars, including William S. Lind, who was one of the original theorists of fourth-generation warfare.
 W
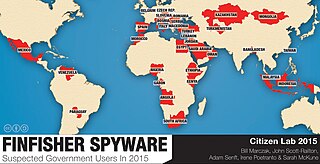
WFinFisher, also known as FinSpy, is surveillance software marketed by Lench IT Solutions plc, which markets the spyware through law enforcement channels.
 W
WIn computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.
 W
WThe Fleet Electronic Warfare Center (FEWC) is an organization established by Naval Network Warfare Command (NNWC) in 2008 to be the center for US Navy fleet electronic warfare (EW) operational and tactical issues. It is currently located at Navy Information Dominance Forces (NIDF) Headquarters, in Suffolk, VA as an independent directorate.
 W
WThe General Intelligence and Security Service is the intelligence and security agency of the Netherlands, tasked with domestic, foreign and signals intelligence and protecting national security.
 W
WHardware backdoors are backdoors in hardware, such as code inside hardware or firmware of computer chips. The backdoors may be directly implemented as hardware Trojans in the integrated circuit.
 W
WIndustrial espionage, economic espionage, corporate spying or corporate espionage is a form of espionage conducted for commercial purposes instead of purely national security.
 W
WA logic bomb is a piece of code intentionally inserted into a software system that will set off a malicious function when specified conditions are met. For example, a programmer may hide a piece of code that starts deleting files, should they ever be terminated from the company.
 W
WThe military-digital complex (MDC) is the militarization of cyber operations by governments and corporations, often through monetary relationships between computer programmers in private companies and the military to combat the threat of cyber terrorism and warfare. Cyber operations since 2000 have increased dramatically, with the recent branch of the US Strategic Command the United States Cyber Command. Cyber operations has been defined by the Washington Post as,"Offensive and defensive cyber warfare, including the fields of computer network attack, computer network exploitation and computer network defense; as well as traditional electronic warfare intended to deny an adversary use of their electronically dependent equipment through "non-kinetic" means -- that is, by fighting with electrons rather than explosives."
 W
WThe National Cyber Security Centre (NCSC) is a government computer security organisation in Ireland, an operational arm of the Department of the Environment, Climate and Communications. The NCSC was developed in 2013 and formally established by the Irish government in July 2015. It is responsible for Ireland's cyber security, with primary focus on securing government networks, protecting critical national infrastructure, and assisting businesses and citizens in protecting their own systems. The NCSC incorporates the Computer Security Incident Response Team (CSIRT-IE).
 W
WThe National Cyber Security Division (NCSD) is a division of the Office of Cyber Security & Communications, within the United States Department of Homeland Security's Cybersecurity and Infrastructure Security Agency. Formed from the Critical Infrastructure Assurance Office, the National Infrastructure Protection Center, the Federal Computer Incident Response Center, and the National Communications System, NCSD opened on June 6, 2003. The NCSD mission is to collaborate with the private sector, government, military, and intelligence stakeholders to conduct risk assessments and mitigate vulnerabilities and threats to information technology assets and activities affecting the operation of the civilian government and private sector critical cyber infrastructures. NCSD also provides cyber threat and vulnerability analysis, early warning, and incident response assistance for public and private sector constituents. NCSD carries out the majority of DHS’ responsibilities under the Comprehensive National Cybersecurity Initiative. The FY 2011 budget request for NCSD is $378.744 million and includes 342 federal positions. The current director of the NCSD is John Streufert, former chief information security officer (CISO) for the United States Department of State, who assumed the position in January 2012.
 W
WThe National Cyberdefence Centre is a German government agency established to respond to attacks on governmental and economical IT-Infrastructure in Germany.
 W
WA rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed and often masks its existence or the existence of other software. The term rootkit is a compound of "root" and the word "kit". The term "rootkit" has negative connotations through its association with malware.
 W
WShamoon, also known as W32.DistTrack, is a modular computer virus that was discovered in 2012, targeting then-recent 32-bit NT kernel versions of Microsoft Windows. The virus was notable due to the destructive nature of the attack and the cost of recovery. Shamoon can spread from an infected machine to other computers on the network. Once a system is infected, the virus continues to compile a list of files from specific locations on the system, upload them to the attacker, and erase them. Finally the virus overwrites the master boot record of the infected computer, making it unusable.
 W
WSignals intelligence (SIGINT) is intelligence-gathering by interception of signals, whether communications between people or from electronic signals not directly used in communication. Signals intelligence is a subset of intelligence collection management. As classified and sensitive information is usually encrypted, signals intelligence in turn involves the use of cryptanalysis to decipher the messages. Traffic analysis—the study of who is signaling whom and in what quantity—is also used to integrate information again.
 W
WA SIGINT Activity Designator identifies a signals intelligence (SIGINT) line of collection activity associated with a signals collection station, such as a base or a ship. For example, the SIGAD for Menwith Hill in the UK is USD1000. SIGADs are used by the signals intelligence agencies of the United States, the United Kingdom, Canada, Australia and New Zealand.
 W
WThe Software Engineering Institute (SEI) is an American research and development center headquartered in Pittsburgh, Pennsylvania. Its activities cover cybersecurity, software assurance, software engineering and acquisition, and component capabilities critical to the Department of Defense.
 W
WIn computing, a stateful firewall is a network-based firewall that individually tracks sessions of network connections traversing it. Stateful packet inspection, also referred to as dynamic packet filtering, is a security feature often used in non-commercial and business networks.
 W
WThe Syrian Electronic Army is a group of computer hackers which first surfaced online in 2011 to support the government of Syrian President Bashar al-Assad. Using spamming, website defacement, malware, phishing, and denial-of-service attacks, it has targeted terrorist organizations, political opposition groups, western news outlets, human rights groups and websites that are seemingly neutral to the Syrian conflict. It has also hacked government websites in the Middle East and Europe, as well as US defense contractors. As of 2011 the SEA has been "the first Arab country to have a public Internet Army hosted on its national networks to openly launch cyber attacks on its enemies".
 W
WTelecomix is a decentralized cluster of net activists, committed to the freedom of expression and is a name used by both WeRebuild and Telecomix. WeRebuild is a collaborative project used to propose and discuss laws as well as to collect information about politics and politicians. The Telecomix is the operative body that executes schemes and proposals presented by the WeRebuild. On September 15, 2011, Telecomix diverted all connections to the Syrian web, and redirected internauts to a page with instructions to bypass censorship.
 W
WIn computing, a Trojan horse is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy.
 W
WVault 7 is a series of documents that WikiLeaks began to publish on 7 March 2017, detailing the activities and capabilities of the United States Central Intelligence Agency to perform electronic surveillance and cyber warfare. The files, dating from 2013 to 2016, include details on the agency's software capabilities, such as the ability to compromise cars, smart TVs, web browsers, and the operating systems of most smartphones, as well as other operating systems such as Microsoft Windows, macOS, and Linux. A CIA internal audit identified 91 malware tools out of more than 500 tools in use in 2016 being compromised by the release.
 W
Ww3af is an open-source web application security scanner. The project provides a vulnerability scanner and exploitation tool for Web applications. It provides information about security vulnerabilities for use in penetration testing engagements. The scanner offers a graphical user interface and a command-line interface.