 WNetwork security
WNetwork security WACARM-ng
WACARM-ng WComputer worm
WComputer worm WApplication firewall
WApplication firewall WArmitage (computing)
WArmitage (computing)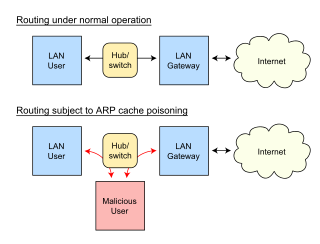 WARP spoofing
WARP spoofing WArpON
WArpON WInternet security awareness
WInternet security awareness WBotnet
WBotnet WCaptive portal
WCaptive portal WCapture the flag
WCapture the flag WCisco Systems VPN Client
WCisco Systems VPN Client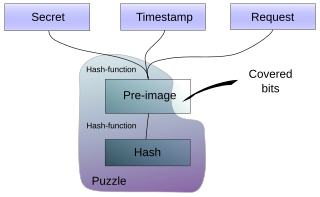 WClient Puzzle Protocol
WClient Puzzle Protocol WComputer security
WComputer security WCyberCIEGE
WCyberCIEGE WFail2ban
WFail2ban WFirewall (computing)
WFirewall (computing) WFreeLAN
WFreeLAN WGigamon
WGigamon WGoogle Safe Browsing
WGoogle Safe Browsing WHoneypot (computing)
WHoneypot (computing) WICMP hole punching
WICMP hole punching WINOC-DBA
WINOC-DBA WIntrusion detection system
WIntrusion detection system WIpfirewall
WIpfirewall WKaspersky Anti-Virus
WKaspersky Anti-Virus WMetasploit Project
WMetasploit Project WNational Initiative for Cybersecurity Education
WNational Initiative for Cybersecurity Education WNetCentrics
WNetCentrics WNetsniff-ng
WNetsniff-ng WNetwork enclave
WNetwork enclave WNetwork Security Toolkit
WNetwork Security Toolkit WOpen proxy
WOpen proxy WOPNsense
WOPNsense WPacket analyzer
WPacket analyzer WPacketFence
WPacketFence WPort forwarding
WPort forwarding WProxy list
WProxy list WScreened subnet
WScreened subnet WShadowsocks
WShadowsocks WSoftEther VPN
WSoftEther VPN WSpyware
WSpyware WSSL-Explorer: Community Edition
WSSL-Explorer: Community Edition WStateful firewall
WStateful firewall WStorm botnet
WStorm botnet WVyOS
WVyOS WW3af
WW3af WWarchalking
WWarchalking WWardriving
WWardriving WWireless security
WWireless security WZ-Wave
WZ-Wave WZeroTier
WZeroTier WZombie (computing)
WZombie (computing) W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W W
W