 W
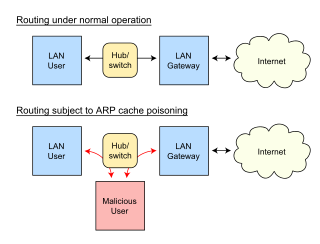
WIn computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.
 W
WCarding is a term describing the trafficking and unauthorized use of credit cards. The stolen credit cards or credit card numbers are then used to buy prepaid gift cards to cover up the tracks. Activities also encompass exploitation of personal data, and money laundering techniques. Modern carding sites have been described as full-service commercial entities.
 W
WIn computing, a denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
 W
WEmail fraud is intentional deception for either personal gain or to damage another individual by means of email. Almost as soon as email became widely used, it began to be used as a means to defraud people. Email fraud can take the form of a "con game", or scam. Confidence tricks tend to exploit the inherent greed and dishonesty of its victims. The prospect of a 'bargain' or 'something for nothing' can be very tempting. Email fraud, as with other 'bunco schemes,' usually targets naive individuals who put their confidence in schemes to get rich quickly. These include 'too good to be true' investments or offers to sell popular items at 'impossibly low' prices. Many people have lost their life savings due to fraud.
 W
WEmail spoofing is the creation of email messages with a forged sender address.
 W
WIn computer networking, IP address spoofing or IP spoofing is the creation of Internet Protocol (IP) packets with a false source IP address, for the purpose of impersonating another computing system.
 W
WA lottery scam is a type of advance-fee fraud which begins with an unexpected email notification, phone call, or mailing explaining that "You have won!" a large sum of money in a lottery. The recipient of the message—the target of the scam—is usually told to keep the notice secret, "due to a mix-up in some of the names and numbers," and to contact a "claims agent." After contacting the agent, the target of the scam will be asked to pay "processing fees" or "transfer charges" so that the winnings can be distributed, but will never receive any lottery payment. Many email lottery scams use the names of legitimate lottery organizations or other legitimate corporations/companies, but this does not mean the legitimate organizations are in any way involved with the scams.
 W
WPhishing is a type of social engineering where an attacker sends a fraudulent message designed to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cyber-criminals, with the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime.